FIRST LOOK:Pentester Academy
Written on October 26th, 2019 by |3ASS3XE
If You Aren’t PenTesting…Try Harder?
Those of you who are familiar with OSCP’s age-old adage of “try harder” have undoubtedly come across web platforms with grandiose claims like “Zero to Hacker” or “Become a Pentester”. Not to take away from the teaching capabilities of the flock, but at some point, it becomes difficult to find quality over quantity. Pentester Academy by SecurityTube (Twitter: @SecurityTube) steps up to the plate in delivering premium content for a low price. The monthly cost of Pentester Academy fluctuates but generally hovers around $39.99, with an initial payment of $99.99. While not as cheap as some of its competitors, it provides users with an interactive lab platform and over 40 updated technical courses accompanied by step-by-step virtual machine environments. These courses are highly technical in content and require a level of curiosity outside the normal check the box training.
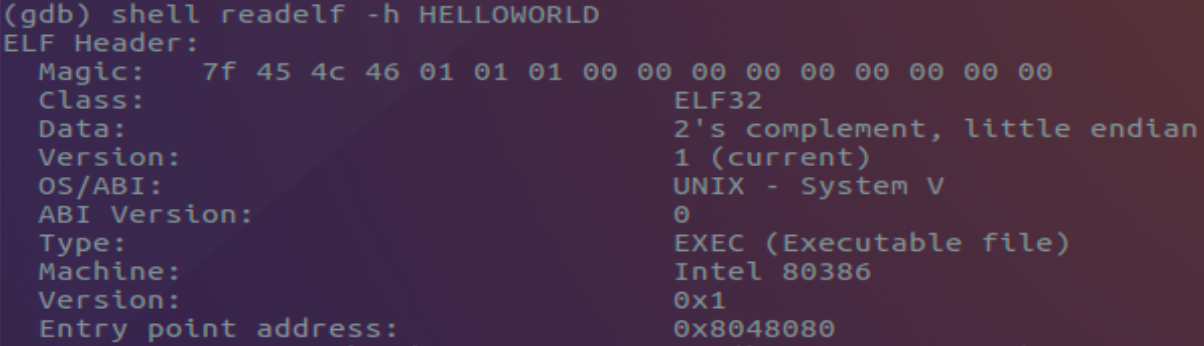
Taking the SecurityTube Linux Assembly Expert (SLAE32) course for 32-bit shell coding, I was immersed in fundamental topics of assembly and debugging and quickly found myself learning Shellcode injection and application memory exploitation. While it took a significant amount of time investment to complete the 20-odd two-modules course, a lot of that time was focused on repeating exercises and doing outside research on exploit development on my own accord. At some stages, I even found myself perusing other classes like GDB Primer and Reversing 32 Bit Linux to satisfy my curiosity and close any knowledge gaps that existed. The learning material for this initial course was far from “cookie-cutter” and felt like a gateway into deeper security topics to hone one’s skills.
Currently, I am preparing to take my CompTIA PenTest + and will pivot to OSCP certification soon after. Pentester Academy is a great platform to have in one’s arsenal, considering how versatile the security exploitation environment is.
Most of the courses active on Pentesteracademy.com :
- Python for Pentesters
- Attacking and Defending Active Directory
- X86 Assembly Language and Shellcoding on Linux
- 86_64 Assembly Language and Shellcoding on Linux
- Javascript for Pentesters
- Linux Forensics
- Pentesting with Metasploit
- Wi-Fi Security and Pentesting
- Exploiting Simple Buffer Overflows on WIN32
- USB Forensics and Pentesting
- Pentesting IOS Applications
- Linux Rootkits for Red-Blue Teams
- Recon for Red-Blue Teams
- Reverse Engineering for ARM Platforms -Ely Reyes